Microsoft has taken decisive action to secure its Edge browser after discovering that cybercriminals exploited its Internet Explorer (IE) compatibility mode as a backdoor into modern systems. The company confirmed that attackers leveraged vulnerabilities in IE’s aging architecture—specifically its legacy JavaScript engine, Chakra—to bypass security measures and gain unauthorized access to Windows environments.
The move marks a turning point for Microsoft’s long-standing struggle to balance compatibility with security. While IE mode was initially introduced to help businesses transition from Internet Explorer to Edge, its continued reliance on outdated code has now made it a serious target for exploitation.
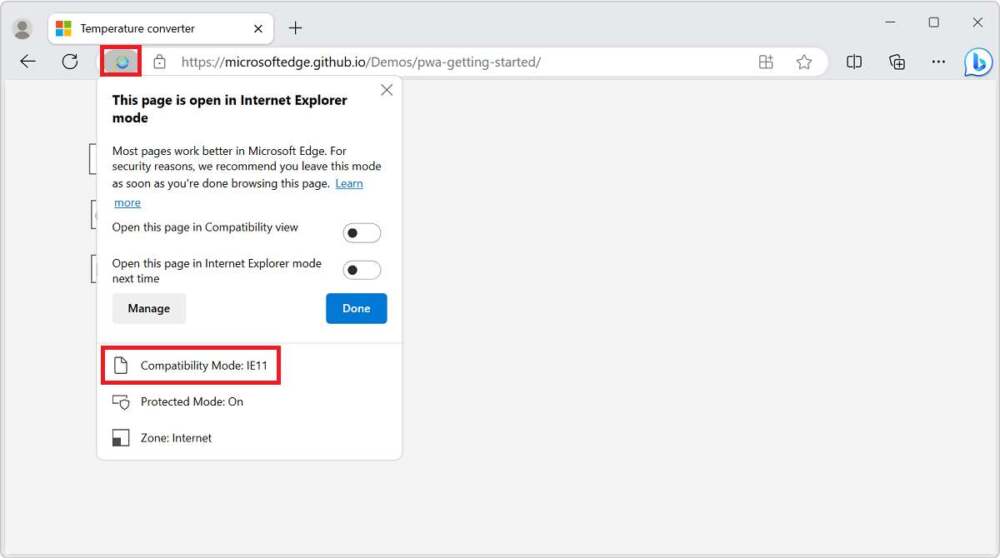
How IE Mode Became a Security Liability
IE mode was designed as a bridge between old and new web technologies. Many enterprises around the world still depend on internal web applications built for Internet Explorer, which uses legacy rendering engines incompatible with modern browsers. To prevent business disruption, Microsoft embedded IE mode into Edge, allowing users to open older websites in a controlled environment while maintaining the modern interface and features of Edge.
However, the company’s good intentions created an unexpected vulnerability. Because IE mode reactivates parts of Internet Explorer’s underlying codebase—including outdated scripting engines—it effectively revives security holes that had long been retired with the old browser.
Security researchers discovered that hackers could manipulate IE mode to force Edge to render certain malicious pages using the IE engine. Once IE mode was engaged, attackers exploited unpatched flaws in the Chakra JavaScript engine to execute arbitrary code. This code allowed them to take control of the affected system, install malware, and in some cases, move laterally across networks to access sensitive data.
In essence, IE mode became a bridge not only for legacy web applications but also for cyber intrusions.
The Exploit Chain: How Attackers Gained Control
According to experts familiar with the investigation, the attack chain typically followed several steps:
- Initial Access – Victims were lured to visit a compromised or malicious website designed to trigger IE mode automatically.
- Exploitation – Using a zero-day vulnerability in the Chakra engine, the attackers achieved remote code execution within the Edge process.
- Privilege Escalation – Secondary exploits allowed them to escape the browser sandbox and gain higher system privileges.
- Persistence – Malicious payloads were then downloaded, enabling ongoing surveillance, data theft, or ransomware deployment.
Microsoft’s internal telemetry detected a rise in these attack attempts earlier this year, particularly targeting enterprise networks in financial services, healthcare, and government sectors—industries that are historically slower to phase out legacy web apps.
Microsoft’s Emergency Response
To mitigate the threat, Microsoft has implemented sweeping restrictions to how IE mode can be accessed in Edge. Key changes include:
- Removal of the IE Mode Toolbar Button: Users will no longer see the quick toggle to reload sites in IE mode.
- Disabled Context Menu Options: The right-click “Open in IE mode” option is now turned off by default.
- Administrative Whitelisting Required: Only websites explicitly approved by system administrators through Edge’s settings can open in IE mode.
- Manual Configuration: Users must go to Edge’s settings and enable the feature under “Default Browser” before any site can load with IE compatibility.
This shift turns IE mode from a simple convenience into a controlled, deliberate function—one that requires administrative oversight and user awareness.
Microsoft described the change as part of a “security-first modernization strategy,” emphasizing that legacy compatibility should never compromise overall browser integrity.
Impact on Businesses and IT Departments
The lockdown will likely cause friction for enterprises that still rely on web-based tools built for Internet Explorer. Many organizations have been slow to migrate due to cost, complexity, or regulatory constraints tied to specific legacy systems.
IT departments are now being urged to:
- Conduct an audit of all internal web applications using IE mode.
- Transition critical systems to modern, standards-based platforms.
- Restrict IE mode access strictly to verified internal domains.
- Implement endpoint monitoring to detect unauthorized IE mode usage.
While these new measures could create short-term inconvenience, cybersecurity analysts argue they’re necessary to prevent far more severe consequences. With hackers increasingly exploiting outdated technologies, the days of “just keeping old systems running” are rapidly coming to an end.
The Bigger Picture: The Cost of Legacy Dependence
This incident serves as a stark reminder of how legacy software, even when hidden inside modern applications, remains a ticking time bomb. Cybercriminals are known to hunt for these outdated components precisely because they’re less frequently maintained and harder for users to monitor.
Microsoft’s situation mirrors challenges faced by other tech giants, from Oracle’s Java runtime vulnerabilities to Adobe’s now-defunct Flash Player exploits. All illustrate the same dilemma: businesses want stability and continuity, but that stability often comes at the cost of security innovation.
As Microsoft continues its push toward a fully Chromium-based future, the company has made clear that IE mode will eventually be phased out entirely. Until then, its use will be tightly restricted and monitored.
User Guidance: What You Should Do
For individual users and businesses alike, Microsoft recommends the following best practices:
- Avoid IE Mode unless absolutely necessary. Only use it for essential legacy applications.
- Update Edge and Windows immediately. Apply the latest patches to mitigate any potential exploit paths.
- Check enterprise policies. Ensure your IT department has explicitly approved any site running in IE mode.
- Adopt modern web solutions. If possible, transition away from web applications that rely on outdated technology stacks.
- Be cautious online. Avoid clicking prompts asking to reload a site in IE mode unless you are certain it’s a trusted source.
A Legacy Finally Closing
The Internet Explorer brand was officially retired in 2022, but its echoes have persisted through IE mode. Now, as the last remnants of that code face active exploitation, Microsoft appears ready to accelerate its departure from the past.
The tightening of IE mode security is not just a patch—it’s a signal that the era of tolerating legacy browser technology is coming to an end. In the modern cybersecurity landscape, even a small piece of history can be weaponized.
With these latest measures, Microsoft aims to ensure that nostalgia no longer becomes a vulnerability.











Leave a Reply